Uncovering the Darknet
The darknet is considered the Wild West of the Internet and for decades has been a haven for both cyber-criminals and those seeking refuge from the prying eyes of authorities.
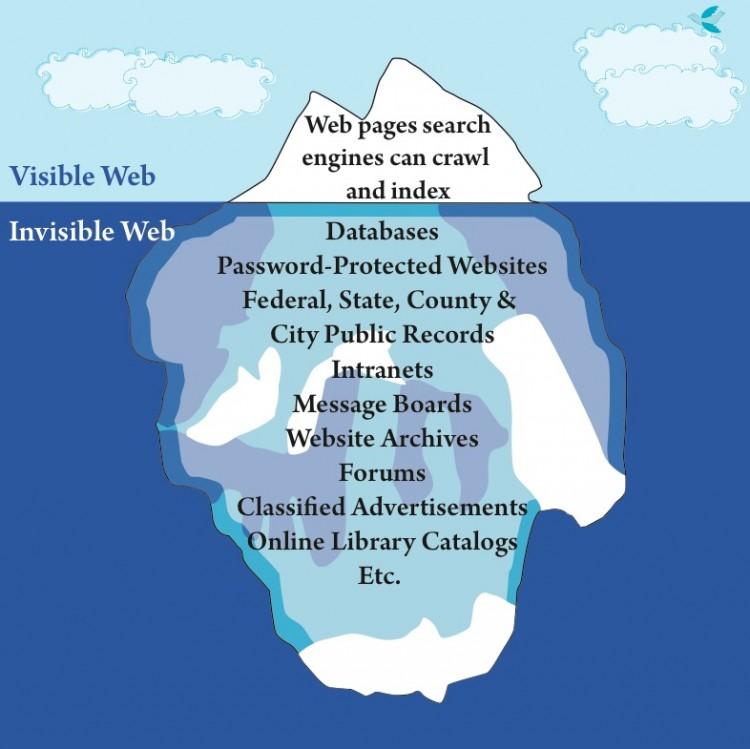
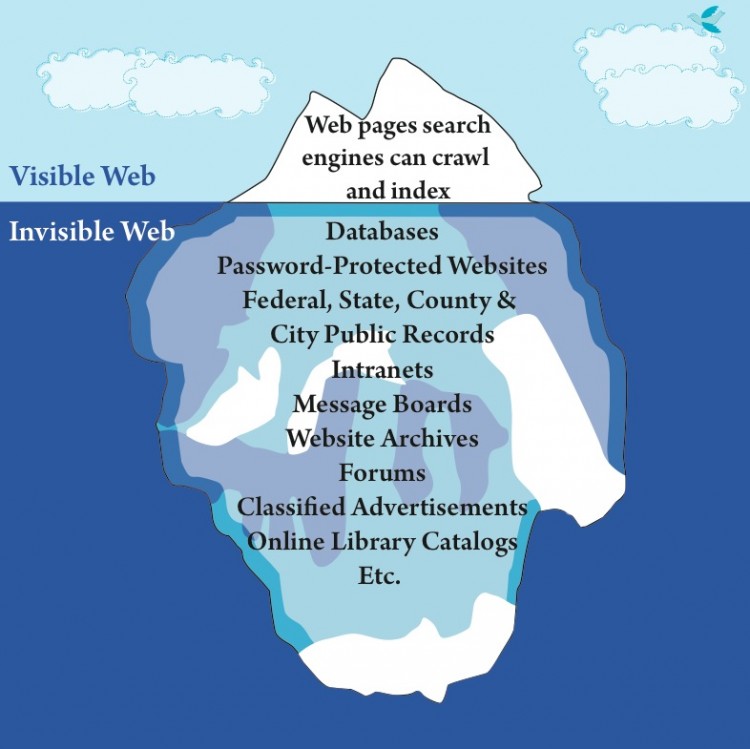
An image representing the 'visible' and 'invisible' Internet. The Epoch Times

Jack Phillips
Breaking News Reporter
|Updated:
Jack Phillips is a breaking news reporter who covers a range of topics, including politics, U.S., and health news. A father of two, Jack grew up in California's Central Valley. Follow him on X: https://twitter.com/jackphillips5
Author’s Selected Articles