Strong Evidence Points to China as Cyberhack Source
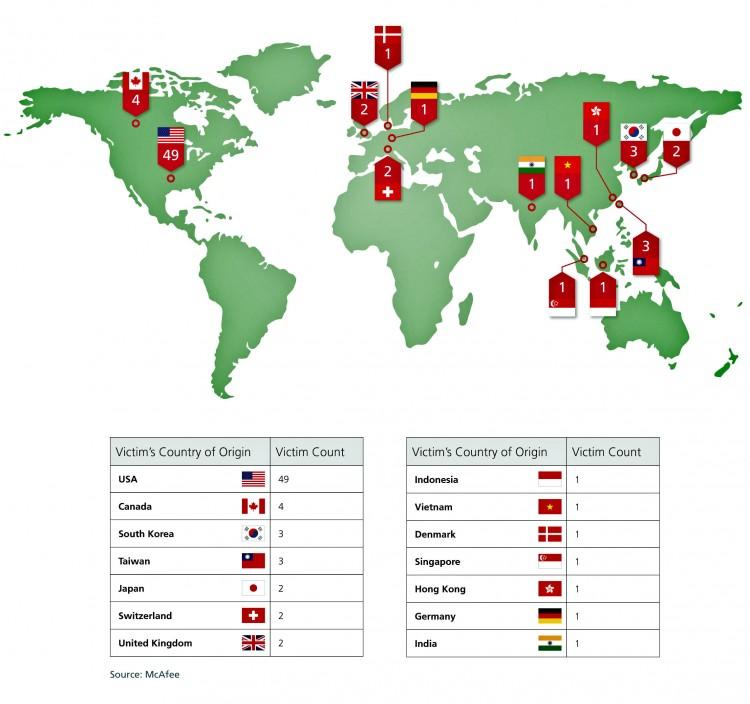
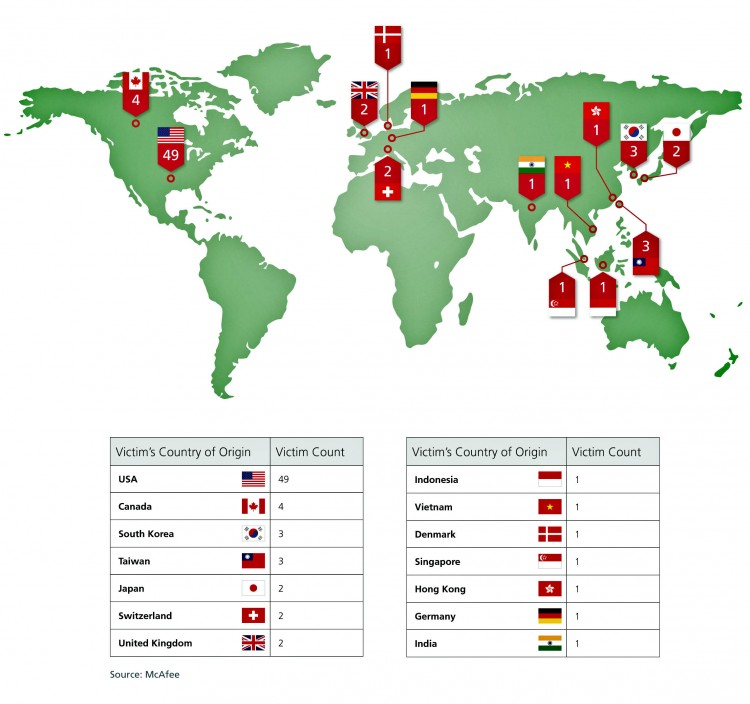
When considering the cyber-onslaught known as Operation Shady RAT, a plethora of evidence points towards the Chinese regime as the culprit, including the attack’s origins having been traced to two cities: Shanghai and Beijing.
|Updated:
Matthew Robertson is the former China news editor for The Epoch Times. He was previously a reporter for the newspaper in Washington, D.C. In 2013 he was awarded the Society of Professional Journalists’ Sigma Delta Chi award for coverage of the Chinese regime's forced organ harvesting of prisoners of conscience.
Author’s Selected Articles