Additional hacker groups are planning to join the recent wave of global cyberattacks that have so far hit thousands of organizations—including factories, banks, and government agencies—in more than 150 countries, affecting more than 300,000 computers. Meanwhile, cybersecurity experts have been scrambling to determine who was responsible for the first wave of attacks.
“There are people copycatting the malware as of right now to try to get on the gravy train,” said Michael Gafford, CEO of Equation Security, a darknet intelligence and software company.
Some of the chatter, according to Gafford, is taking place on cybercrime forums on the darknet, and Equation Security also has intercepted communications of a known “specific faction” that is discussing joining in as well. The darknet is an alternate internet, only accessible with specialized software, that has marketplaces and forums used by criminal groups to buy, sell, and conspire.
Hackers are also already altering the virus code to create new attacks. Darknet data collected by William Welna, co-founder of Equation Security, shows that efforts to add additional functions to the WannaCry malware used in the attacks are already well underway. Gafford said they’ve already seen around six different variants.
WannaCry spreads between computers by exploiting a known Windows vulnerability and does not require the user to make a mistake—unlike most forms of malware—in order to infect the machine.
After the computers are infected, the cybercriminals behind the attacks then lock the systems down and charge the owners a fee to regain access, using what’s referred to as ransomware.
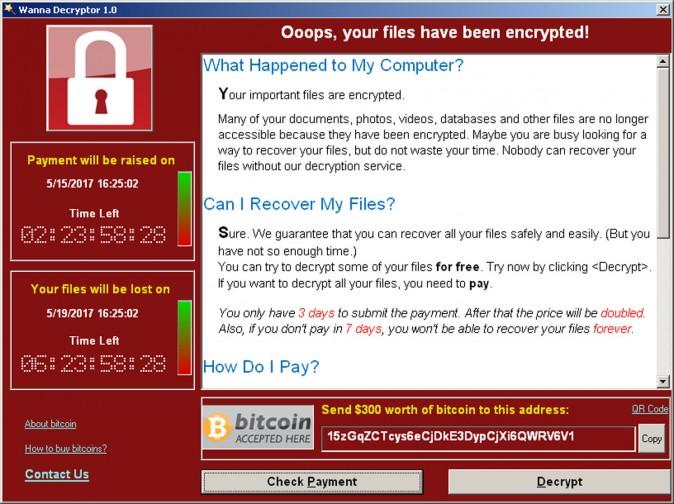
Users affected by WannaCry attacks receive an alert on their computers stating, “Ooops, your files have been encrypted!” A window beneath tells users how to pay the ransom to unlock their machines and recover their files. It also shows a timer counting down the seven days they’ve been given to make the payment. It threatens users that a “free event” in six months awaits anyone who doesn’t pay.